Trojan Slayer is a security product that protects the system against malware. It works by creating a list of programs that are allowed to function unfettered and blocks the applications that are unknown to the utility.
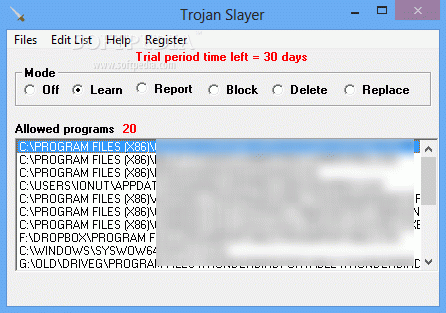
The tool brings to the table a simple to use interface that features the main options in the upper part. Users can stop its activity at any time in order to lift the program restrictions.
For the application to establish a defense line the most commonly used programs have to be run. This way, Trojan Slayer learns which of them are allowed to run.
Once it is in report mode it automatically alerts the user when it detects activity from a utility that is not on the safe list. There is the possibility to turn off the unauthorized software.
Should this operation have no effect there is the alternative to delete it, which initiates the removal procedure. If this is still not successful, Trojan Slayer can be used to replace the file with a dummy one, thus preventing the malware from being restored.
Apart from just reporting unwanted activity the utility has the ability to automatically perform actions such as blocking, deleting and replacing the files that have not been authorized to run.
A log with all the events is maintained by the program so its activity can be verified at any time by the user. Also, it features the possibility to edit the list of accepted programs and remove those that have been added by accident or that are no longer available on the computer.
Bianca
grazie mille per il crack
Reply
fixxxer
working serial. thanks
Reply
Nadia
salamat sa inyo para sa keygen Trojan Slayer
Reply
giovanna
thank you for the patch
Reply